
(Updated February, 2017) Nowadays, a lot of people are depending on the internet to do just about anything. In recent years, there has been an increasing number of users who want to maintain their privacy while online for various reasons. Due to the immense technological advancements, various internet platforms are able to capture plenty of information about internet users which some people find uncomfortable especially depending on the sites an individual is visiting. For those who wish to remain anonymous, Tor browser is a famous platform that enables internet users to hide their identity.
Interestingly, a lot of countries across the globe have been investigating the Tor network and trying to unmask information about tor web browser users. For instance, since the introduction of Tor browser in 2012, both U.S. and Russia have been at the forefront of launching campaigns against the use of Tor to the extent of offering rewards to anyone who can decode the platform and expose it.
So What Exactly is Tor Browser and Why Is It Controversial?
In this article, we shall discuss the definition of Tor, is Tor browser safe as well as how it is beneficial for internet users. Basically – a Tor browser review!
As earlier mentioned, Tor browser is a free software that enables users to conceal their identities while using the internet. The key difference between tor and other standard browsers such as private modes or incognito is that the Tor browser security makes it untraceable.
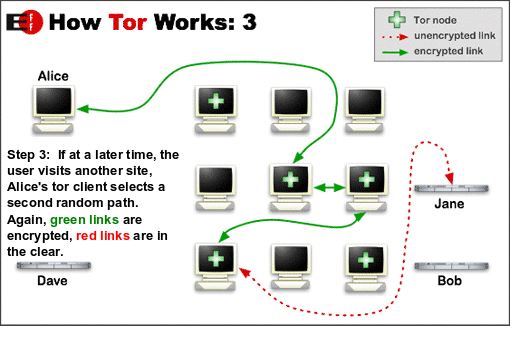
It is easy to access Tor, just like downloading any other software, you need to visit a Tor browser download link and initiate the download and installation process. Tor works using a mechanism known as anonymization. Using anonymity software the information that is sent by users over an online network is encrypted and transmitted in multiple layers to other computers. Every relay is transmitted one after the other until the entire information gets to its destination. Using a Tor browser prevents other people from obtaining information about your online activities including sites you visit. Furthermore, the Tor network completely conceals your physical location.
There is common misconception that internet users who use Tor browser are often engaging in unscrupulous and illegal activities; this is not true. The Tor network is designed for anyone who is keen on maintaining their privacy while online. In recent years, there has been mounting concern that internet users confidential information is being used by some site owners without user authorization.
You May Also Like: Is The Apple Watch All That Great?
For instance, top websites including some social media sites have been discovered to be sharing users browsing history with advertisers and other third party platforms. As a result, internet users end up getting a lot of ads and solicitation emails with users’ personal information included; this is a sign that some sites are analyzing users and passing information to third parties. Because of this, the number of users installing and using Tor browser has gone up recently.
How to Use a Tor Web Browser and Who Uses Tor Web Browser?
The good news is that this browser is fully compatible with different gadgets. For instance, you can comfortably install and use a Tor browser Android or Tor browser Mac version; it all depends on the device you’re using. In light of this, there are different groups of people that rely on Tor browser for basic security functions.
Journalists and activists use Tor browser to file reports of injustices and human rights violations confidentially without exposing themselves and to safeguard their information sources. Whistleblowers can also use Tor browser to highlight cases of corruption and still manage to remain anonymous. Tor browser is useful in the family as parents can install it for their children to protect their identities while using the internet. Adults can also use this platform to protect their dignity and identity while using various online platforms.
Professionals and corporate entities are also embracing tor network for purposes of maintaining confidentiality especially when sharing confidential documents whose contents need to be protected from unauthorized third parties. Protection of browsing history is essential because some internet providers sell client browsing records and even log-in data to third party users.
The military also use the Tor network because of the sensitive nature of their jobs. Critical tasks such as the intelligence gathering and field agents in most cases have to remain undercover during their assignments and keep secret all their online communications. For businesses, a Tor web browser is essential because it helps firms to confidentially search for information about their competitors, keep their business strategies a secret as well as encourage accountability.
On many occasions, people are compelled to use Tor network because of the increasing risks associated with remaining identifiable while using internet platforms. Fortunately, Tor network permits users to bypass firewalls and anonymously visit sites such as Facebook.
How Do You Begin Using the Tor Network?
The simplest way to become a Tor browser user is to make use of the Tor browser bundle. It is easy to configure a Tor browser download from Tor’s official website via Mozilla Firefox. After the download for the browser has completed, a message appears asking if you’d like to continue to configure the Tor browser. It’s important to mention that due to its nature of operation, Tor at times can violate usage policies of certain sites and public networks.
For those using networks with firewalls, you can get a tor browser download link by sending an email to [email protected] with “help” as the email subject. Once this is done, you’ll receive step-by-step guidance email on how to download tor browser. Before commencing, it’s always good to verify that your tor browser is on and you’re using the internet anonymously.
The browsing tips for Tor browser are simple; first and foremost, every user should read the guidelines immediately after Tor browser download to know what is expected of them. If you are using Tor, be aware that you cannot use any browser plugins such as RealPlayer, Quicktime, Flash and others because they always reveal a user’s IP address. Installation of addons and plugins is highly discouraged because there is a high chance of them interfering with the browser’s stability.
You Might Also Like:What are the Best Smartphones for 2016?
While on the Tor network, it is always advisable to visit sites via HTTPS. Tor automatically activates the HTTPS feature but it’s still good to be watchful of URLs you’re visiting. Opening or trying to access downloaded materials while using Tor browser is also discouraged; disconnect from the internet before opening these files. If you like using torrents, be advised that it’s not safe to use them when browsing with Tor web browser. As a general guideline, it makes sense to invite the people you communicate with to use Tor browser in order to achieve maximum effectiveness.
The only problem with using Tor browser is that it may, in some cases, slow down internet speed because it has to configure several relays to conceal your identity. Overall, Tor browser is a good option for users who appreciate online privacy. Have you used Tor browser and how? Let us know in the comments below!